I usually write about search marketing, analytics and conversion optimization, but I felt it was important to share a discovery I made recently.
I noticed a major phishing scam hijacking the paid search ads of financial and banking companies on brand keywords. The activity was discovered by an alert I received from BrandVudu, a third-party risk compliance and brand protection tool.
The alert uncovered paid search ads that look like official bank or credit card brand ads, but when a consumer clicks the ad, the landing page is a phishing website.
In this example the tactic follows this pattern:
1. An ad is triggered on brand or brand-plus searches for popular bank and credit card keywords (e.g., brand + “ login” or “low APR credit card offers”)
2. The ad contains a display URL for the financial institution, and therefore appears genuine and official.
3. Consumers who click on the ad are misdirected to a phishing site which attempts to get the user to call a phone number. After this the following events take place:
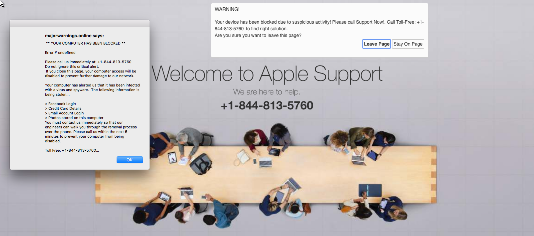
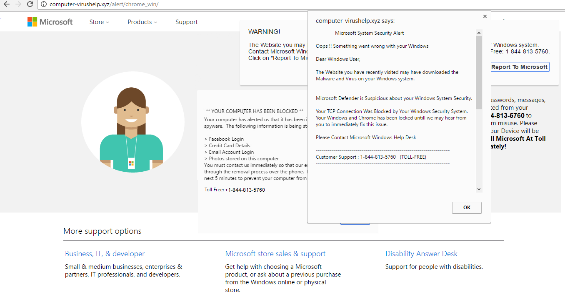
- The site claims that malware has been downloaded onto the user’s machine, along with a troubling pop-up, and loud sound effects including warning bells.
- The user is directed to call 844-813-5760 or 800-646-0707, which identifies the virus as the ZEUS virus, in order to get assistance from either Apple or Microsoft support.
- In some cases, the pop-up or the tab can be easily closed. In other cases, the entire computer screen is blocked by the warning message and the only way to get out of it, if you are a Windows user, is to use Task Manager to kill your browser program.
- The landing page looks like the below, depending on whether you are a Mac or Windows user:
BrandVudu identified the following URLs where consumers are being directed. These URLs seem to rotate daily, with new URLs being used every few days:
Destination URL Landing Page Date Detected Knowdailyhoroscope.com majorwarnings.online/alert/chrome_win March 6, 2017 Freedictionarydefinition.com virushelp.xyz/alert/chrome_win March 6, 2017 clickingads.online helpvirus.xyz/alert/chrome_win March 2, 2017 thesaurus-dictionaryonline.com pc-helps.xyz/network7026/chrome_win March 2, 2017 Source: BrandVudu
Why aren’t these scams being caught?
Misleading ads are a problem, as evidenced by the 2016 Bing Ads Quality Review showing millions of ads needing to be blocked. You would think that popular malware solutions would find these phishing scams and alert users, right?
I thought the same thing, but a scan of the above Destination URLs using several top malware scanners revealed green “all-clear” good grade for each site.
The phishing sites are fooling the scanning companies by misdirecting the scanner to a legitimate URL. When they’re visited by a crawler used by malware scanner tools, they usually send users to the actual financial institution website. Scans are performed and land on the legitimate site, therefore a good grade is returned.
Specifically what happens is the phishing site performs a check on the visitor and sends the visitor in one of two directions:
- If the visitor is an anti-virus scanner or ‘crawler’, the visitor is pushed to the proper financial institution landing page or other real site, which looks legitimate and fine; or
- If the visitor is a person (i.e. using a detectable browser), then the phishing site directs the user to the malware phishing site.
This misdirection is the likely culprit as to how the phishing scam can circumvent the search engine’s own audit checks.
The financial implications for bank advertisers
While you might view this simply as a nuisance to be expected in the world of online ad fraud, the implications are in fact much more serious. Financial institutions could potentially be subject to regulatory inquiries plus the erosion of good will in their brand names.
The Consumer Financial Protection Bureau (CFPB), for example, is the government watchdog that makes sure financial ads are not taking advantage of consumers. They’ve been very active in the last two years, filing multi-million-dollar lawsuits against offenders.
Further, the lawsuits are made public, so even if advertisers can pay the fine, they suffer a huge black eye in the press with already wary consumers.
Takeaway
If you are on the paid search team of a financial institution, government site, or credit card company, it is recommended that you take the following steps to ensure your ads are not being attacked:
- Use a third-party risk assessment tool to monitor your brand and brand plus keywords. There are many options for this; I used information from BrandVudu for this article. Other tools include The Search Monitor, iSpionage and AdGooroo
- Report issues to the search engine’s trademark compliance team for immediate take down
- Document your findings to protect against an audit by a regulatory agency.
If you are reading this article and you are a search engine e.g. Google or Bing, your editorial teams may need additional tools to catch these scams.
Source: How URL hijackers are disrupting banks’ PPC campaigns | Search Engine Watch
502.822.6695
team@guardianowldigital.com


Recent Comments